Concept Review (Volunteer Mentor/Tutor)
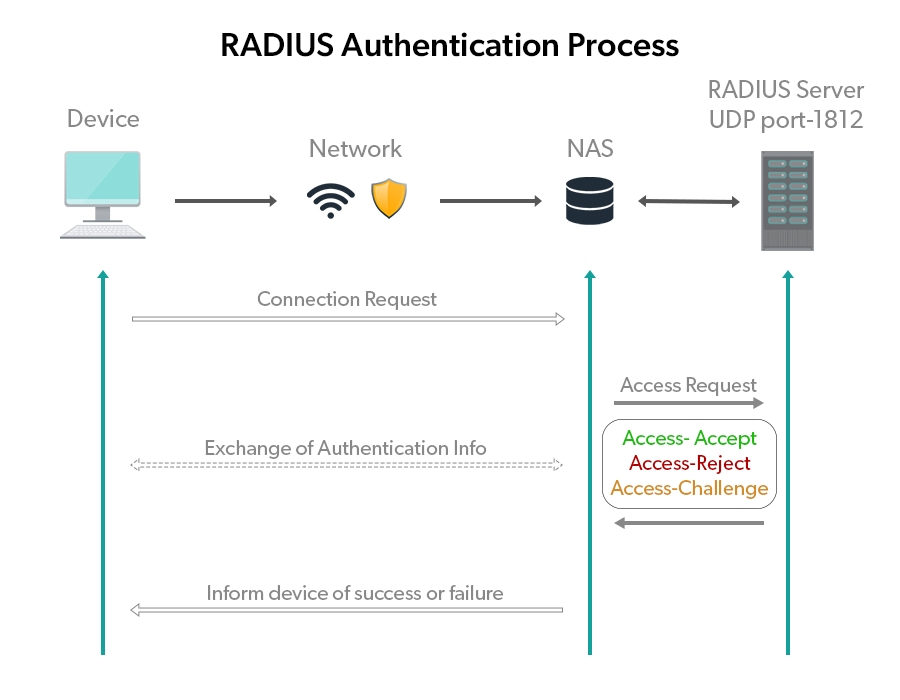
- What is RADIUS?
- Remote Authentication Dial-In User Service
- It provides functionality similar to AD, so what does Active Directory do?
- You can configure RADIUS to protect access to all kinds of resources: a server, a wifi network, etc..
- Each user becomes responsible for their own credentials and as an administrator you're now responsible for a centralized solution making it easier for you to manage.
-
What is Cross Site Scripting vs SQL Injection
-
There are concepts shared between them, but how you accomplish the two are quite different. High-level injection is the use of SQL against an unsanitized webpage/application to gain unauthorized access by abusing the intention of a SQL query/command. XSS or Cross Site Scripting is accomplished by managing to execute malicious JS or similar on a webpage to perform a malicious action, could be stealing tokens, changing where credentials are sent, etc..
-
SQL Injection examples https://www.hacksplaining.com/lessons/sql-injection/log-window
-
XSS examples: https://learn.snyk.io/lesson/xss/
-
-
What is EAPoW?
-
Well first, what is EAP? Extensible Authentication Protocol (EAP)
-
Authentication protocol not an encryption protocol this is how it differs from say WEP. Its the authentication protocol used inconjunction with RADIUS
-
EAPoW is just the protocol specific to use over WiFi
-
-
What is content filtering?
- Allowing or blocking trraffic based on data insidee packet (Application section of packet)
- Types of filtering:
- Web site filtering
- Blocking filesharing websites
- Block malicious sites (potentially malicious sites)
- parental control
- Email filtering
- URL filtering
- Web site filtering
-
What is a configuration baseline?
- All kinds of configuration baselines, but usually you want to standardize the configurations of both your user devices and servers, so you create a baseline. Everyone should have these applications, these security configs in place, these shortcuts etc...
-
What is a hardened configuration?
- Hardened configuration is the practice of building a secure baseline configuration for again both user devices and servers, ensuring no unnceessary ports are open, ensuring users cannot get into BIOS, or can't install certain applications, windows firewall is on and configured, etc..
-
What are packets and frames how do they differ?
- Packets function at layer 3 of the OSI model. They contain information necessary for routing which includes a source/destination IP address. When we're talking about packets, we're talking about routing them between networks. This is why they rely on a router, to pass them between autonomous systems.\
- Frames function at layer 2 of the OSI model. They contain MAC headers and trailers because they are handled by a switch. Switches have no concept of different networks or routing, they just send frames of data to/from the specified mac addresses.
- What is PCIe slot of motherboard for?
- Peripheral Component Interconnect Express
- Components that require high speed data exchanges, but can be used for just about anything, similar to a USB port
-
Is use of PCIe is optional ?
- Completely optional
-
What is VoIP?
- (voice over IP) Phones that aren't connected to telephone lines the way they used to be, but instead use ethernet ( internet) to make calls.
-
RAID configuration:how is it on a ssd ? Clarify this question for me
-
Is RAID configured on actual physical disks?
- No, it is configured in either the BIOS for the hardware raid card or a software type RAID is configured within the OS, ie. Windows 11
-
Do regular pc’s still have physical hdd or are ssd in there?
- Both are physical. HDD are just older models with spinning magnetic disks used to store data, solid states are more like flash drives in how they function.
-
What is TKIP?
- TKIP (Temporal Key Integrity Protocol) is a security protocol used to secure wireless computer networks. It was developed as an improvement over the original WEP (Wired Equivalent Privacy) protocol to address its vulnerabilities. TKIP was introduced as part of the WPA (Wi-Fi Protected Access) standard
- TKIP is a security protocol used to protect Wi-Fi networks from unauthorized access and data theft. It's like a lock on your Wi-Fi door. Here's how it works:
- Dynamic Keys: Instead of using the same key all the time (which is what WEP did and got hacked easily), TKIP changes the key for each piece of data sent over the network. It's like changing the lock on your door every time someone comes in or out.
- Mixing Things Up: TKIP mixes up the key with other info, like the name of your Wi-Fi network and a unique number for each piece of data. This makes it harder for hackers to figure out the key.
- Checking for Tampering: TKIP also checks to make sure nobody's tampered with the data being sent. It's like having a security camera to catch any funny business
-
What are file systems?
-
At a high level a file system is just a system of organization of your files/folders by a computer. Some are good at handling lots of small files others a few large. There are many different types in use, often for legacy purpose (continued support of old systems). There are nearly deprecated file systems that have almost 100% superior newer iterations.
-
What is the different between FAT32 & NTFS?
-
FAT32: File Allocation Table 32 - it's an old and simple 1990s Microsoft file system. It uses a file allocation table to track where it stores files, hence the name (F)ile (A)llocation (T)able with a max volume size of 32GBs, meaning no partitions larger than 32GBs each.
-
NTFS : New Technology File System - A new more advanced file system designed to overcome many of the limitations of FAT32. Provide features such as folder permissions, encryption, and disk quotas as well as much, much, larger file/partition sizes.
Port Mapping/Port Forwarding Example:
Minecraft Server (Port 25565): The user's computer within the home network hosts a Minecraft server, which is configured to listen on port 25565 for incoming connections from players. The internal IP address of the user's computer running the Minecraft server is, for example, 192.168.1.10.
Port Forwarding Configuration: The user configures port forwarding on their home router to forward incoming traffic on port 25565 to the internal IP address of their computer hosting the Minecraft server (192.168.1.10). This configuration tells the router that any incoming traffic on port 25565 should be redirected to the Minecraft server running on the internal IP address.
Ultimately I, the friend of the minecraft hoster could then connect my client to their public IP, the one there router has (everyone's home router has) at the specified port, and I would be able to reach inside their LAN network and hit their server.
Tags: Technology Fundamentals Concepts